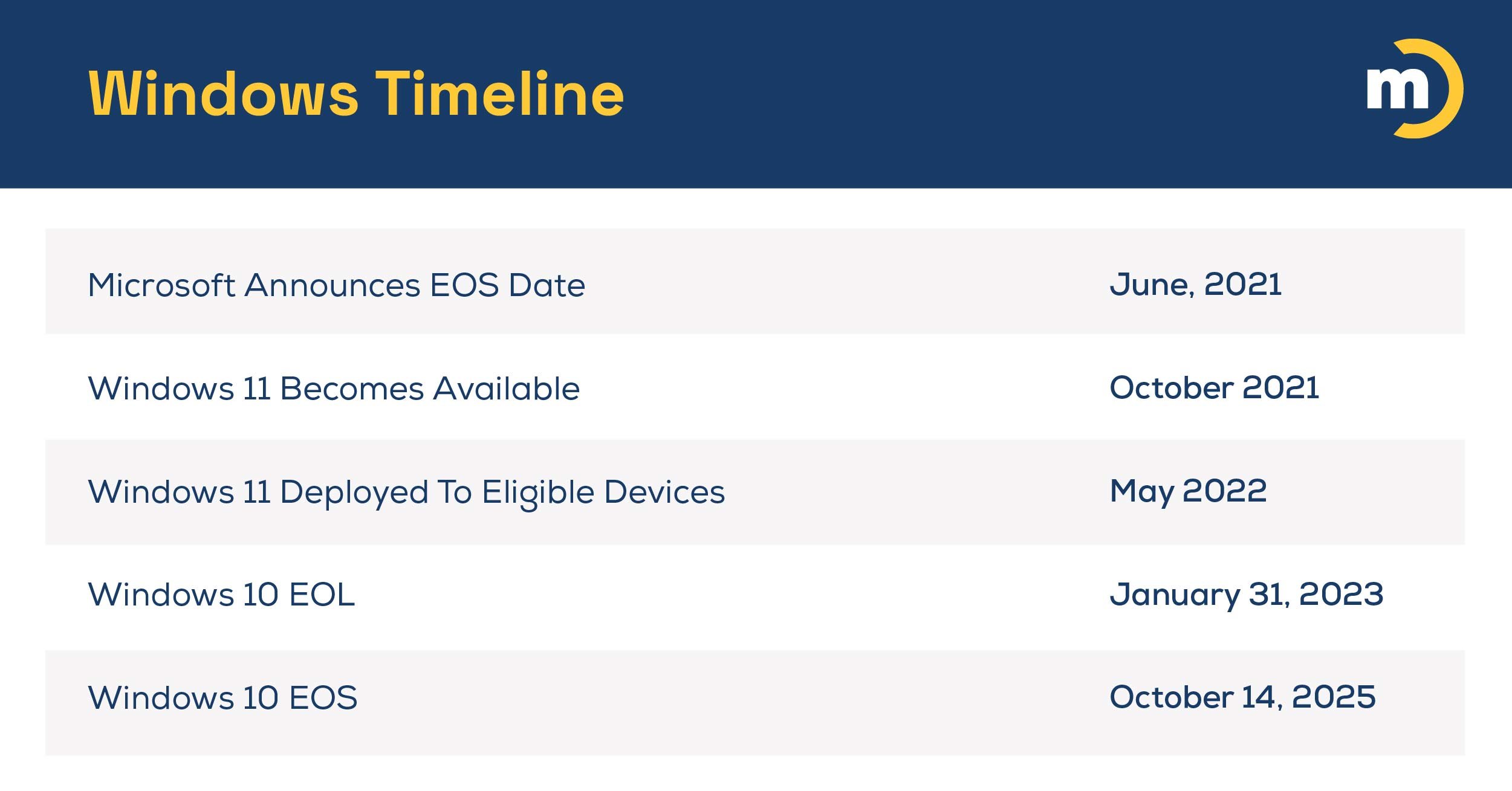
What the St. Paul Cyberattack Means for Local Government Cybersecurity Throughout the US
The recent ransomware attack on the City of St. Paul should be a wake-up call for municipal governments nationwide.…
Cybersecurity Best Practices for Smart Factories
Let's be honest — if you're running a manufacturing operation today, you're probably thinking about smart factory t…
A CISO's Roadmap for Law Firm Cybersecurity in 2025 — Q&A
Law firms handle some of the most sensitive information in the business world, making them prime targets for cyberc…
Mastering Cybersecurity Compliance in Regulated Industries
First off, I just want to say that I’ve never met a business owner who was happy about having to comply with regula…
Why AI Code Security Is Keeping Cybersecurity Teams Up at Night
Let's be honest — the thought of using AI-generated code is pretty slick. Tools like OpenAI's Codex can crank out f…
5 Ways To Get Phishing and Security Awareness Training Right, 1 Way To Get It Wrong
You may have seen a stat like this before: 91% of all cyberattacks begin with a phishing email. So logically, you’d…
Key Takeaways From KnowBe4's Phishing Threat Trends Report [Ungated]
KnowBe4 recently released its 2025 Phishing Threat Trends Report. It’s 20 pages long, and it’s gated, so I’ve boile…
Top Cybersecurity Laws and Regulations To Know About in 2025
Many companies are now facing the challenges posed by malicious hackers attacking their IT environment. Unfortunate…
Everything You Should Know About the Dark Web
You’ve probably already heard of the dark web, or you wouldn’t be reading this.