In addition to using strong and unique passwords, Multi-Factor Authentication (MFA) is vital to maintaining account security as it requires users to prove their identity in more than one way, which we call factors.
As Microsoft defines it, a factor in authentication is a way of confirming your identity when you try to sign in. For example, a password is one kind of factor, it's a thing you know. The three most common kinds of factors are:
- Something you know - Like a password, or a memorized PIN.
- Something you have - Like a smartphone, or a secure USB key.
- Something you are - Like a fingerprint, or facial recognition.
How Effective Is Multi-Factor Authentication?
Even within the most common types of multi-factor authentication, the relative security of each method varies. Some forms of MFA are simply stronger than others. For example, codes sent by text can be intercepted by hackers, or stolen via a SIM swap attack. Soft token MFA (e.g., receiving a code via an application on your smartphone) through a provider like Duo is more secure because they remove a number of attack vectors, and a physical security key is better still.
Regardless, even the weakest of these methods, SMS-authentication, offers significantly stronger security than a password alone, and experts believe that multi-factor authentication can still prevent as much as 80-90% of cyberattacks. This is why most cyber insurance carriers require MFA — it’s not just best practice, it’s an essential practice.
Why Isn't MFA Enough?
No single cybersecurity tool or practice is enough to prevent all attacks. While MFA blocks up to 99.9% of account-related attacks, because almost all phishing attacks are automated, hackers don’t need a high success rate to do real damage. Furthermore, with more targeted, sophisticated attacks, their success rate increases significantly.
Multi-factor authentication can go a long way, but just as quickly as new cybersecurity tools become available, hackers try to find new ways to defeat them. Cybersecurity is a rapidly evolving field, and cybercriminals often outpace solutions that were once considered the gold standard. It’s an ongoing battle that can only be won with constant adaptation.
Are Office 365 Accounts With MFA Vulnerable?
In a word, yes. Recently, Microsoft identified a serious new threat to accounts, even those with MFA already set up. Through an extensive phishing campaign, hackers have applied an effective, if not sinister, way to gain access to these user accounts and have targeted more than 10,000 organizations since September. Once hackers gain access to these email accounts, they can launch subsequent Business Email Compromise (BEC) attacks in order to commit fraud.
How Exactly Are Hackers Still Gaining Access?
Hackers can intercept communications between a server and a legitimate user through a proxy site. When a user enters their password, that proxy site will faithfully relay that information to the server they’re trying to access, as well as the server’s response. Once the user is verified, even if MFA is used, the hacker can steal the resulting session cookie and use that information to access the account.
Like many devastating cyberattacks, this one starts with a simple phishing email containing an HTML attachment leading to the malicious proxy site. It is within this site that a user logs in, completes their MFA prompt, all while giving the attacking website these two factors without even realizing it is not a legitimate login.
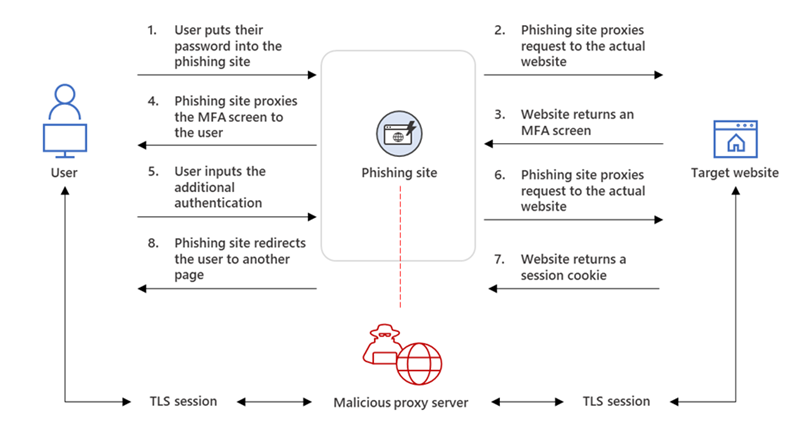
Figure | AiTM Phishing Website Intercepting the Authentication Process from Microsoft Blog published July 2022
Once an attacker is in control of an account, they can access other email accounts and send messages designed to fool recipients into wiring funds to scammers. In some cases, the user remains entirely unaware because the attacker’s system even deletes the sent messages from the sent and trash folders.
The Importance of Ongoing Training
Most people are overconfident in their ability to spot a scam, but six out of ten Americans are highly vulnerable to phishing emails. Because these attacks start with a simple phishing email, training your employees to be suspicious of emailed links, even those that appear to be sent by coworkers, is an effective defense strategy. Security Awareness Training can be highly effective, in some cases reducing the percentage of phish-prone employees to just 5%.
It's also important to remember that we are all potentially vulnerable to making careless decisions from time to time. Depending on the organization, staff members may frequently struggle to manage their existing workload and might not have the additional time required to evaluate every single email with extreme care. And while it’s always good practice to hover over a link before clicking it, sometimes even legitimate login pages can have odd-looking URLs.
How To Keep Your Organization Safe
The best approach to cybersecurity is holistic, relying on multiple layers of security tools and practices to keep hackers out, and block and tackle cybersecurity controls to recognize attacks in progress quickly and neutralize them. In addition to MFA and ongoing training, it’s important to prioritize critical patches and upgrades, and restrict user access to only those systems, tools, and data they need to do their job effectively.
Fortunately, no organization needs to reinvent the wheel regarding robust cybersecurity. Organizations like The National Institute of Standards and Technology (NIST) and the Center for Internet Security (CIS) have compiled lists of cybersecurity best practices.
If you’re wondering if your organization is in line with their recommendations, a Cybersecurity Assessment from Marco can identify any vulnerabilities in your technologies and processes, so they can be addressed before a hacker can take advantage of them.
Learn more about a Cybersecurity Assessment
