How Cybercriminals Are Bypassing Multi-Factor Authentication
In addition to using strong and unique passwords, Multi-Factor Authentication (MFA) is vital to maintaining account…
Benefits of Wide Format Printing
Those who say print is dead haven’t talked to many marketers. Thanks to the human brain’s heavy emphasis on visual …
Common Cyber Attacks
There’s been a 300% rise in cybercrime in the U.S. since 2020. The numbers make for sensational headlines, but the …
Unified Communications in the Cloud vs. On-Premise
Unified Communications (UC) can help you get so much more from your phone system. If you’ve already decided that UC…
6 Reasons To Make the Switch to Outsourced IT Services
Outsourced IT is trending. Small to midsize businesses have quickly adopted managed IT as the complexity of today’s…
Why Voice over IP Is Better for Your Small Business
When you operate a small business, every dollar counts. While it’s often easy to identify large, unnecessary expend…
Quick Fixes for Poor Quality Printing Results
We’ve all encountered poor quality printing results at one time or another. And even though we now have self-drivin…
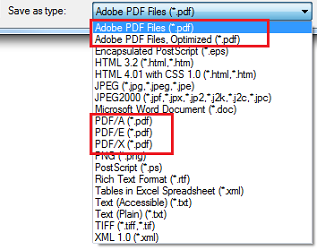
8 Types of PDF Standards – Each Serves a Unique Purpose
Many people are familiar with PDF files; you’ve probably accessed a PDF recently or even created one. PDF stands fo…
Microsegmentation Provides Additional Layers of Data Security
While digital data storage solutions are often seen as the root cause of data breaches, the problem pre-dates the i…