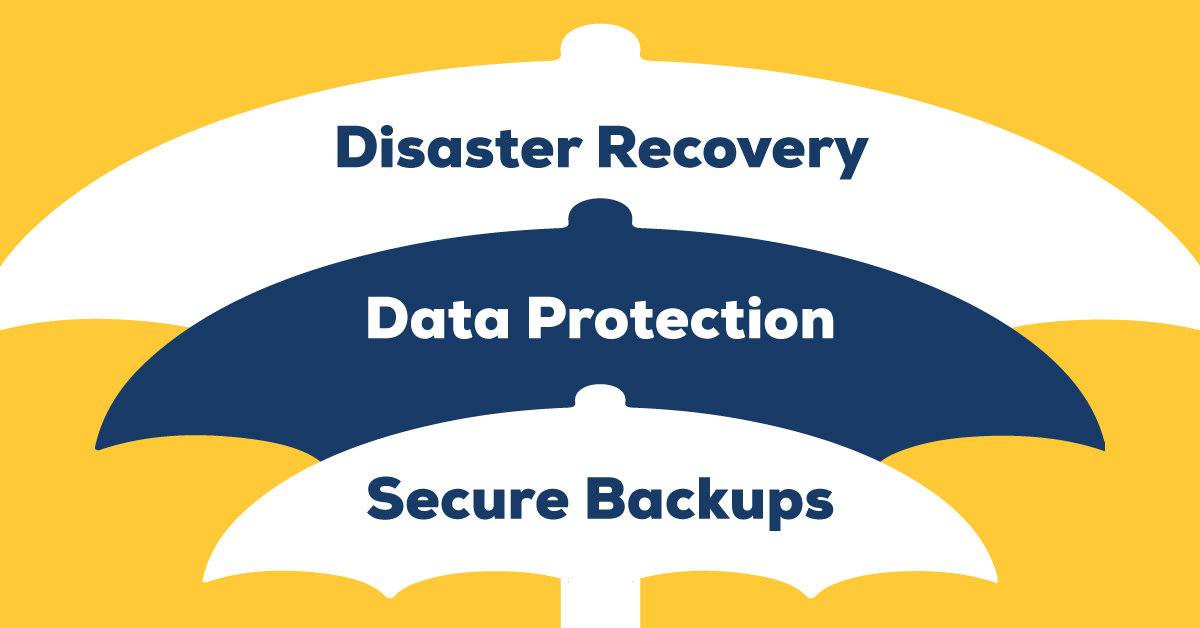
Important Cybersecurity Terms
You may have noticed that technology folks speak quickly and use acronyms almost constantly. What can I say? It’s p…
Vendor Due Diligence: 101
When many IT pros think about cybersecurity, they tend to focus on potential risks within their organization’s syst…
Secure Access Service Edge (SASE)
“Migrate to the cloud,” they said. “Everything will be easier,” they said.
Top Small Business Cyberattack Vulnerabilities
Is your small business protected from cyberattacks? If you have to ask, the answer is probably no. Too many small b…
Why You Should Invest in Email Protection
In films, cybercriminals are primarily depicted as some sort of genius-level keyboard ninjas, feverishly typing awa…
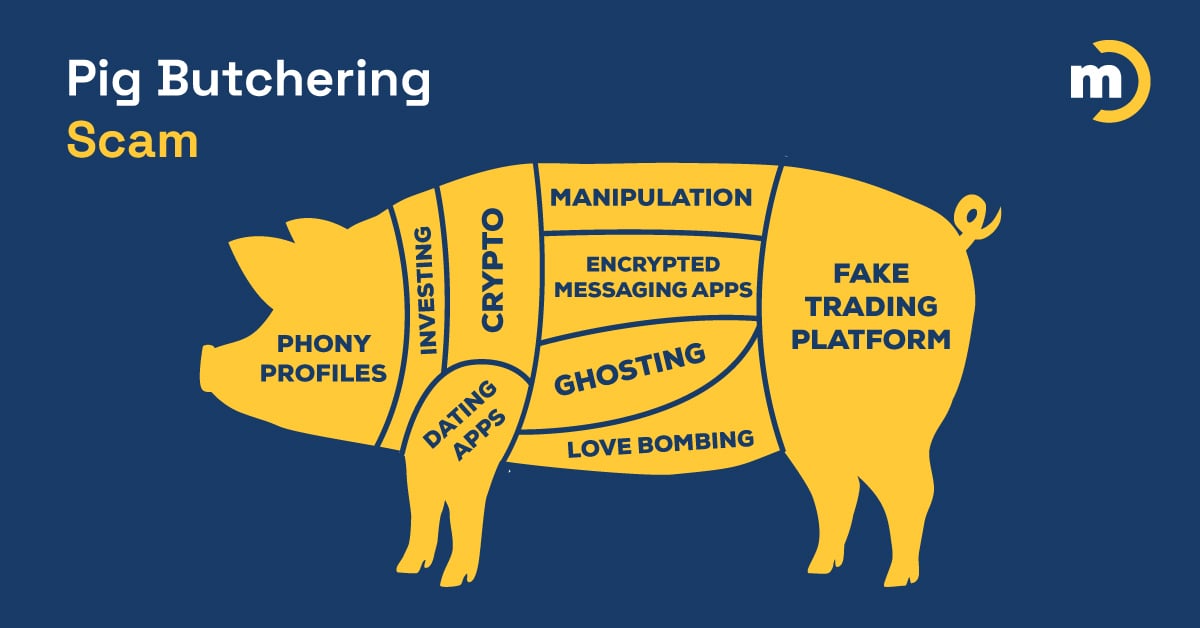
This New Social Engineering Scam “Fattens You Up” Before the Slaughter
One of the most disgusting aspects of cybercrime is just how easy it is for criminals to make a killing from it.
Ransomware — A Top Small Business Security Vulnerability
If your business hasn’t yet experienced a ransomware attack, but you aren’t actively preventing one, you’ve been ve…
How to Improve Your Cybersecurity Posture in 2023
While the supply chain is loosening, and other acute side-effects of the pandemic continue to subside in most parts…