What You Need To Know About Recent Apple Updates for Vulnerability
Have you updated the software on your Apple device lately? If not, look for any new software updates and install th…
What Is Your Incident Response Plan?
What is your Incident Response Plan? An Incident Response Plan (IRP) should contain everything your organization wi…
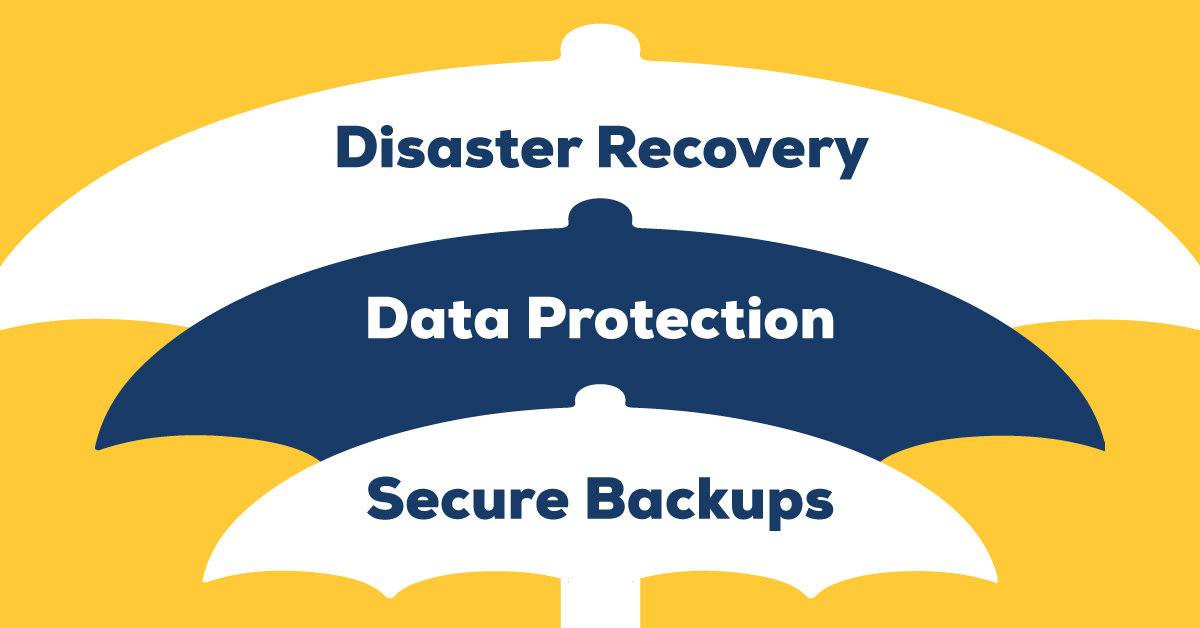
How Layers of Cybersecurity Can Protect Your Business
The National Institute of Standards and Technology (NIST) defines Defense-in-Depth (DID) as “An information securit…
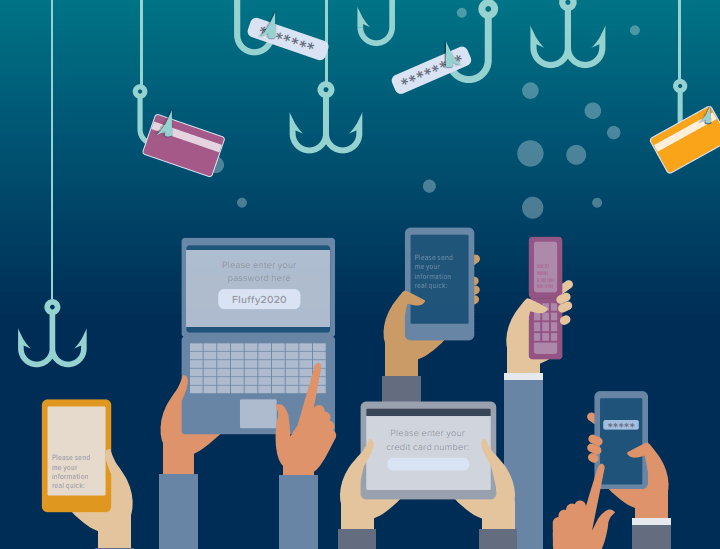
What Is Smishing and Why Is It a Problem?
Smishing is much like traditional phishing scams, except these messages are sent by text (SMS) instead of email. Ty…
What Is a Business Continuity Plan, and Why Do You Need One?
Odds are, you won’t be struck by lightning today, and the odds are also against your workspace being destroyed toda…
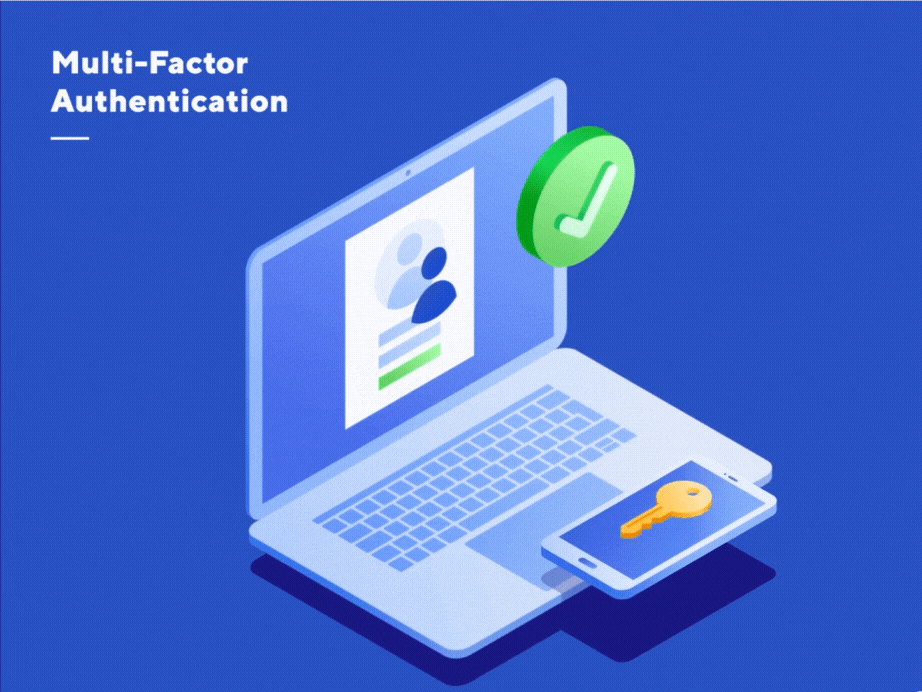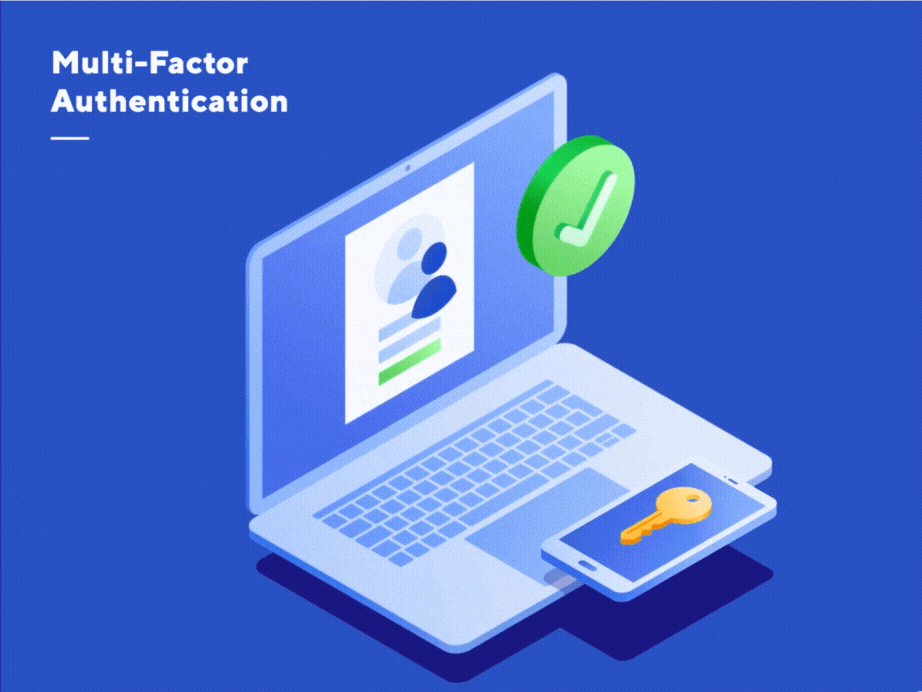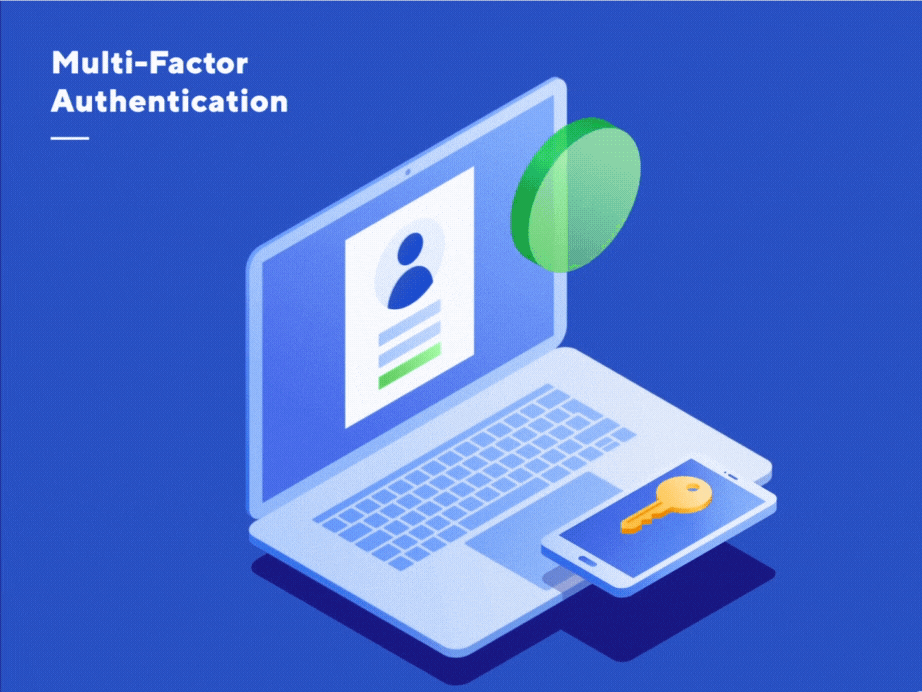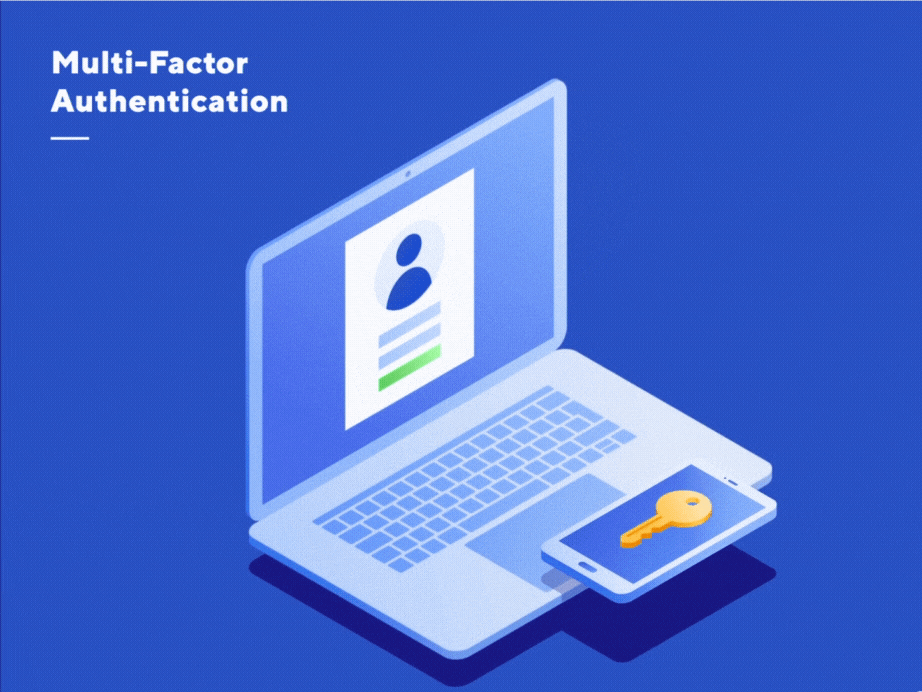
How Cybercriminals Are Bypassing Multi-Factor Authentication
In addition to using strong and unique passwords, Multi-Factor Authentication (MFA) is vital to maintaining account…
Common Cyber Attacks
There’s been a 300% rise in cybercrime in the U.S. since 2020. The numbers make for sensational headlines, but the …
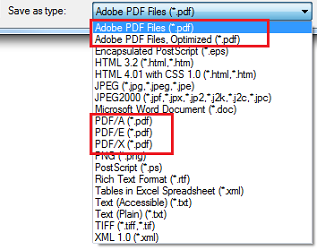
8 Types of PDF Standards – Each Serves a Unique Purpose
Many people are familiar with PDF files; you’ve probably accessed a PDF recently or even created one. PDF stands fo…
Microsegmentation Provides Additional Layers of Data Security
While digital data storage solutions are often seen as the root cause of data breaches, the problem pre-dates the i…